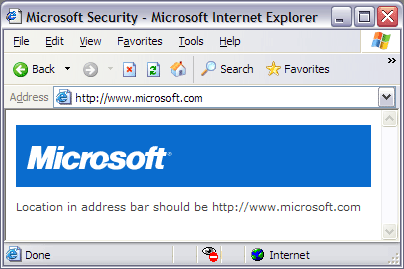
I had my doubts, but the URL spoofing bug in IE that Microsoft is supposedly investigating is really there. The link-happy blogosphere, filled with copy-and-paste addicts, is a ready victim to this bugger (via Zap The Dingbat).
Test Exploit
The bug is caused by simply inserting '%01' in front of '@' character in URLs like foobar@blahblah.com to hide the real domain name from the fake one which goes in front of the '%01' (see the HTML source for this post).
As an architect, this sort of bugs takes a lot of energy out of me. Ever feel betrayed by the ground you walk on? It's like discovering that everything you designed was built on a gigantic turtle that just woke up. I have obviously exaggerated the size of the problem but this sort of bullshit just upsets my stomach.
Another thing that upsets my stomach is getting all excited enough about something to invest months into it just to wake up and realize that there is no reason for people to use it. There is a quite a bit of that in the web services and Atom hypes. Get in the habit of asking Why Would They? if you can't take the disappointments. IT is NOT about YOU, but ALL about THEM, the people who will be using what you build.
Update:
On my IE 6 running on XP with all the latest patches, this is what I see after pressing the "Test Exploit" button.